Research on Fine-grained Detection Method of Honey Pot Contracts Based on LSTM and Fuzzing
Keywords:
LSTM Model, Fuzzing Testing, Smart Contract Honeypot, Fine-grained DetectionAbstract
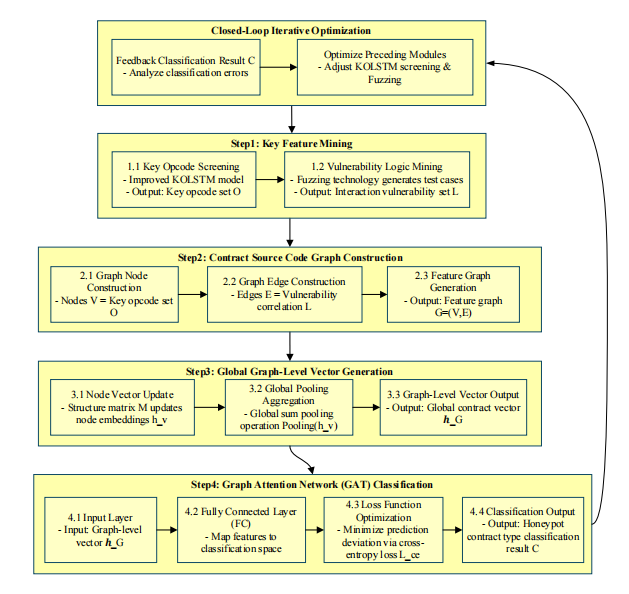
Honey pot contract operation code sequences exhibit strong concealment, significantly increasing detection complexity. To address this, this study proposes a fine-grained detection method based on LSTM and Fuzzing. By analyzing frequency differences across operation codes in different honey pot contract types, we calculate their occurrence rates and assign high initial weights to high-frequency operation codes. The weight mechanism is then integrated into the LSTM model to calculate operational code contribution levels and importance scores, enabling extraction of high-scoring critical operation codes. The research employs Fuzzing fuzz testing technology to generate initial test case sets and defines their deconstruction methods. Using case identifiers and functional codes, we validate interaction logic vulnerabilities in honey pot contracts through mutation factor probability matrices. By constructing source code graph structures using critical operation codes and interaction logic vulnerabilities, we update and aggregate vector nodes with global accumulation pooling functions to generate graph-level vectors. These graph-level vectors are then fed into graph attention networks, with cross-entropy loss functions jointly determining honey pot contract types. Test results demonstrate that the proposed method achieves sub-3 false positives for six honey pot contract types, demonstrating high precision in fine-grained detection.
References
He, D., Wu, R., Li, X., Chan, S., & Guizani, M. (2023). Detection of vulnerabilities of blockchain smart contracts. IEEE Internet of Things Journal, 10(14), 12178-12185.
Zhang Renlou, Wu Sheng, Zhang Hao, & Liu Fangyu. (2025). Slice-GCN: 基于程序切片与图神经网络的智能合约漏洞检测方法[Slice-GCN: An Intelligent Contract Vulnerability Detection Method Based on Program Slicing and Graph Neural Networks]. Journal of Cyber Security, 10(1), 105-118.[in Chinese]
Zhang, L., Li, Y., Guo, R., Wang, G., Qiu, J., Su, S., ... & Tian, Z. (2024). A novel smart contract reentrancy vulnerability detection model based on BiGAS. Journal of Signal Processing Systems, 96(3), 215-237.
Zhang, J., Lu, G., & Yu, J. (2024). A Smart Contract Vulnerability Detection Method Based on Heterogeneous Contract Semantic Graphs and Pre-Training Techniques. Electronics, 13(18), 3786.
Gu, M., Feng, H., Sun, H., Liu, P., Yue, Q., Hu, J., ... & Zhang, Y. (2022, May). Hierarchical attention network for interpretable and fine-grained vulnerability detection. In IEEE INFOCOM 2022-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS) (pp. 1-6). IEEE.
Li, L., Liu, Y., Sun, G., & Li, N. (2023). Smart contract vulnerability detection based on automated feature extraction and feature interaction. IEEE Transactions on Knowledge and Data Engineering, 36(9), 4916-4929.
Liu Fangqing, Huang Han, Xiang Yi & Hao Zhifeng.(2023). 基于流形鸽群优化的智能合约重入性漏洞检测方法研究[Research on Intelligent Contract Reentrancy Vulnerability Detection Based on Manifold Pigeon Swarm Optimization]. Scientia Sinica(Technologica), 53(11),1922-1938. [in Chinese]